There are use-case scenarios when you don’t actually need a full featured VPN connection, but you only need to tunnel your browser through a SSH session. This is extremely easy to do by creating a SOCKS5 tunnel through SSH. Such solution can be called a poor man’s VPN since it isn’t a real VPN, but a proxy connection.
Why would you need to tunnel the browser through SSH?
These are some of the scenarios I can think of:
- You are traveling and you need to access local sites at home without restrictions. So you can enable the remote SSH on your router, if it supports it, then establish a SSH connection to it. This allows you to browse the web using your home IP address and it comes handy to unblock local streaming services or login to your web banking service if the bank restricts access from foreign locations.
- Unblocking streaming services also applies to services in other countries, let’s say that you want to access a UK streaming service like BBC iPlayer and you have a VPS server in UK, or you want to access Hulu using a VPS in USA. The list can go on.
- You need a security & obfuscation layer to bypass potential browsing snooping and censorship, or you just don’t want to reveal your real IP address to some websites.
The good thing about SSH tunneling is that you don’t need to install additional software like a VPN client. On Linux and Mac it works using the system’s SSH client (preinstalled, in most cases). On Windows you can use the PuTTY utility.
How to setup a SSH SOCKS5 tunnel on Linux and Mac
Open the terminal, then connect to your server via SSH and use the SOCKS5 parameter to enable the local SOCKS5 server:
ssh -D8080 user@server The parameter “-D” enables the SOCKS5 local server and it is followed by the local port you want the SOCKS5 proxy to listen on. In my example I used port 8080, you can use any other port you like.
If you run the SSH server daemon on a different port other than default port 22, include the parameter “-p” followed by the port number your SSH servers is using:
ssh -D8080 -p54321 user@serverIn the example above, the SSH server runs on port 54321.
Eventually, you can add the “-N” parameter and it won’t open a shell session, just establish the SSH connection.
How to setup a SSH SOCKS5 tunnel on Windows
On Windows 10, a SSH client is preinstalled so you can connect directly from the cmd.exe terminal. The syntax is the same as it is for Linux/Mac (see above).
On other Windows releases but also on Windows 10 if you don’t want to use the built-in SSH client, you can use the 3rd party SSH utility PuTTY.
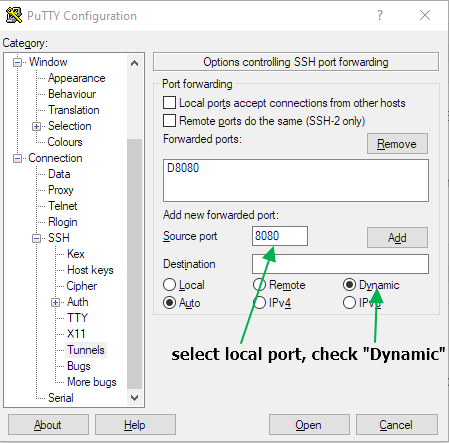
Open PuTTY, add your server IP/hostname and port if other than 22. In the left column menu, open “Connection > SSH > Tunnels” and add the Source Port (the local port SOCKS5 will listen on) select the checkbox “Dynamic” then Add.
Set the SOCKS5 proxy connection in your browser
In Firefox, open Preferences > Network Settings or just search for “proxy” in the upper right corner search box.
Select “Manual proxy configuration”
SOCKS Host: 127.0.0.1
SOCKS Port: 8080 (the local port you’ve set when running SSH)
Enable “Proxy DNS when using SOCKS v5”
This last setting is very important, else Firefox will send the DNS traffic directly instead of using the tunnel.

That’s it. Now see if browsing works and check your IP to make sure that you are indeed tunneling the browser traffic over the SSH tunnel.
